A) Aggregates switch logs for easier review and correlation
B) Polls SNMP-enabled server logs for current status
C) Distributes logging applications to monitoring servers
D) Purges switch logs when they reach capacity
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Ann, a user, reports that her desktop phone is not working on one cable. However, that cable provides connectivity to her laptop. A technician determines PoE is not provided to the end device. Which of the following is MOST likely the cause?
A) Transceiver mismatch
B) Crosstalk
C) Jitter
D) Open/short on the cable
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company wants to implement a wireless infrastructure on its campus to meet the needs of its BYOD initiative. The company has users with legacy devices and wants to accommodate them while delivering speed to other users who have modern systems. Which of the following standards BEST fits these requirements?
A) 802.11a
B) 802.11ac
C) 802.11b
D) 802.11n
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
At which of the following OSI model layers would a router operate?
A) Physical
B) Network
C) Transport
D) Data link
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following additional capabilities does a next generation firewall provide beyond a standard network firewall? (Choose two.)
A) Application control
B) User identification
C) Network address translation
D) Virtual private networking
E) High availability
F) Access control rules
H) B) and F)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Allowing data to be centrally stored and accessed by multiple devices on an isolated subnet is BEST understood as:
A) NAS
B) iSCSI
C) SAN
D) FCoE
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is installing a wireless solution. The solution needs to support new and legacy wireless network clients at the maximum possible speed. Which of the following wireless standards should the technician install?
A) 802.11a
B) 802.11ac
C) 802.11b
D) 802.11g
E) 802.11n
G) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is the physical location where the customer-premise equipment comes together with the ISP or third-party telecommunications equipment?
A) Server room
B) Equipment closet
C) Demarcation point
D) Intermediate distribution frame
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
While logged into a financial application, a user gets errors when trying to write to the database. The network administrator is not familiar with the application and how it communicates with the database. Which of the following documentation types should the network administrator use to troubleshoot the data flow?
A) Logical diagram
B) Physical diagram
C) Network baseline
D) Change management log
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician has been asked to provide daily reports on network saturation. Which of the following would BEST reflect these statistics?
A) Average bandwidth usage
B) Error rate on trunk ports
C) Packet drops to the ISP
D) Processor utilization for the Internet router
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator is assigned to run and connect a Cat 6e Ethernet cable between two nodes in a datacenter. Which of the following connector types should the network administrator use to terminate this cable?
A) DB-9
B) RS-232
C) DB-25
D) RJ-45
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator wants to increase the confidentiality of the system by hardening the authentication process. Currently, the users log in using usernames and passwords to access the system. Which of the following will increase the authentication factor to three?
A) Adding a fingerprint reader to each workstation and providing a RSA authentication token
B) Adding a fingerprint reader and retina scanner
C) Using a smart card and RSA token
D) Enforcing a stronger password policy and using a hand geometry scan
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An end-user device requires a specific IP address every time it connects to the corporate network; however, corporate policy does not allow the use of static IP addresses. Which of the following will allow the request to be fulfilled without breaking the corporate policy?
A) DHCP relay
B) DHCP exclusion
C) DHCP option
D) DHCP reservation
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is setting up the wireless network for a company's new branch office. After doing a site survey, the technician discovers there is a lot of interference from 2.4GHz devices at the location on channel 11. Which of the following would be the BEST channel on which to set up the WAPs?
A) Channel 6
B) Channel 7
C) Channel 9
D) Channel 10
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is running copper cable from a core switch to a network closet that is approximately 574ft (175m) away. Which of the following should the technician use to accomplish this?
A) Bridge
B) Hub
C) Patch panel
D) Load balancer
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network engineer utilizes a box of Cat5e cable in a datacenter for use between 10Gbps switches in a single rack. After the engineer finishes the installation, switch administrators notice random speed drops and intermittent connection issues. Which of the following is this an example of?
A) Incorrect cable type
B) Attenuation
C) Incorrect pinout
D) Bad ports
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is reviewing the following output from a router: 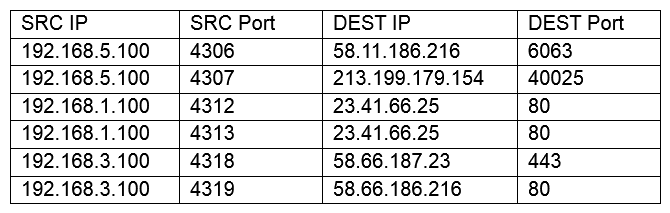 Which of the following is this an example of?
Which of the following is this an example of?
A) A vulnerability scan
B) A port scan
C) A traffic log
D) A packet capture
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician has completed configuration on a new satellite location. The location has a new firewall and a small internal network. The technician has been asked to perform basic vulnerability testing. Which of the following tools would BEST assist the technician in verifying the security of the site?
A) Packet sniffer
B) Bandwidth tester
C) Port scanner
D) Protocol analyzer
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following BEST describes the functionality of the root guard feature on a switch?
A) BPDUs entering the root bridge are ignored.
B) The STP root bridge cannot be changed.
C) Broadcast storms entering from a root port are blocked.
D) Loop protection is enabled on the root port of a switch.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is configuring user access to a VPN concentrator and has been advised to use a protocol that supports encryption over UDP. Which of the following protocols has the technician MOST likely configured for client use?
A) TFTP
B) DTLS
C) DNS
D) SNMP
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 361 - 380 of 829
Related Exams