A) collectLog.cmd
B) LogExport.exe
C) ExportLog.vbs
D) smc.exe
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company is concerned that its clients may be out-of-date and it wants to ensure that all running applications are protected with Symantec's latest definitions, even if they are unavailable on the Symantec Endpoint Protection 12.1 (SEP) client. How could the company configure SEP to achieve this goal?
A) Enable SONAR with High Risk detections set to Quarantine.
B) Enable Insight Lookup as part of a daily scheduled scan.
C) Enable Insight for Community and Symantec Trusted Files.
D) Enable and apply an Intrusion Prevention policy.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which setting can an administrator configure in the LiveUpdate Policy?
A) specific content revision to download from a Group Update Provider (GUP)
B) specific content policies to download
C) Linux Settings
D) frequency to download content
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which action does SONAR take before convicting a process?
A) quarantines the process
B) blocks suspicious behavior
C) reboots the system
D) checks the reputation of the process
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An administrator wants to make sure users are warned when they decide to download potentially malicious files. Which option should the administrator configure?
A) the Notifications tab under the admin-defined scan settings
B) the Notifications tab under Auto-Protect settings
C) the Network Protection Security event notification in location-specific settings
D) the Notifications tab under Download Insight settings
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A large software company has a small engineering department that is remotely located over a slow WAN connection. Which method will deploy the Symantec Endpoint Protection 12.1 (SEP) clients to the remote site using the smallest amount of network bandwidth?
A) Deploy the SEP clients using basic content.
B) Deploy the clients using the Push Install Wizard.
C) Install a Group Update Provider on a remote computer and then install the remote SEP clients.
D) Install a Group Update Provider on a local computer and then install the remote SEP clients.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which Symantec Endpoint Protection 12.1 protection technology provides the primary protection layers against zero-day network attacks?
A) SONAR
B) Client Firewall
C) Intrusion Prevention
D) System Lockdown
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which task is unavailable for administrative accounts that authenticate using RSA SecurID Authentication?
A) reset forgotten passwords
B) import organizational units (OU) from Active Directory
C) configure external logging
D) enable Session Based Authentication with Web Services
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Administrators at a company share a single terminal for configuring Symantec Endpoint Protection. The administrators want to ensure that each administrator using the console is forced to authenticate using their individual credentials. They are concerned that administrators may forget to log off the terminal, which would easily allow others to gain access to the Symantec Endpoint Protection Manager (SEPM) console. Which setting should the administrator disable to minimize the risk of non-authorized users logging into the SEPM console?
A) allow users to save credentials when logging on
B) delete clients that have not connected for specified time
C) lock account after the specified number of unsuccessful logon attempts
D) allow administrators to reset the passwords
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company successfully deploys Symantec Endpoint Protection 12.1 to its clients. However, when the company deploys the client to the servers, the servers immediately reboot. The company needs to prevent the servers from rebooting during normal business hours. What is wrong?
A) The "Hard restart" option is enabled in the Restart Settings tab.
B) The "Restart immediately if the user is not logged in" option is enabled.
C) A previous version of the client was installed.
D) There is "No prompt" configured on the Restart Settings tab.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An exception needs to be created for a file named "RunMe.exe" in a user's Windows 7 "My Documents" folder. The user's login name is Bob. Which method should be used?
A) create a file exception for "RunMe.exe" with a Prefix Variable of [USERNAME]
B) create a file exception for "[Drive]:\Users\Bob\My Documents\RunMe.exe"
C) create a file exception for "*\RunMe.exe"
D) create a file exception for "RunMe.exe" with a Prefix Variable of %USERPROFILE%
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In the virus and Spyware Protection policy, an administrator sets the First action to Clean risk and sets If first action fails to Delete risk. Which two factors should the administrator consider? (Select two.)
A) The deleted file may still be in the Recycle Bin.
B) IT Analytics may keep a copy of the file for investigation.
C) False positives may delete legitimate files.
D) Insight may back up the file before sending it to Symantec.
E) A copy of the threat may still be in the quarantine.
G) A) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company has 10,000 Symantec Endpoint Protection (SEP) clients deployed using two Symantec Endpoint Protection Managers (SEPMs) . Which configuration is recommended to ensure that each SEPM is able to effectively handle the communications load with the SEP clients?
A) Push mode
B) Client control mode
C) Server control mode
D) Pull mode
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An administrator is troubleshooting a Symantec Endpoint Protection (SEP) replication. Which component log should the administrator check to determine whether the communication between the two sites is working correctly?
A) Apache Web Server
B) Tomcat
C) SQL Server
D) Group Update Provider (GUP)
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user is unknowingly about to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client's system. In which feature set order must the threat pass through to successfully infect the system?
A) Download Insight, Firewall, IPS
B) Firewall, IPS, Download Insight
C) IPS, Firewall, Download Insight
D) Download Insight, IPS, Firewall
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 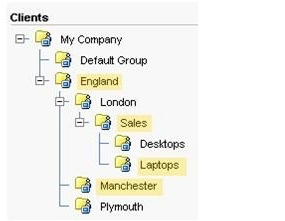 Inheritance is turned on only for groups England, Sales, Laptops, and Manchester (highlighted) . Without turning inheritance off, which top level group must be modified to affect users in the Laptop group?
Inheritance is turned on only for groups England, Sales, Laptops, and Manchester (highlighted) . Without turning inheritance off, which top level group must be modified to affect users in the Laptop group?
A) My Company
B) England
C) London
D) Sales
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A Symantec Endpoint Protection 12.1 client is running a user-defined scan when a scheduled, administrator-defined scan is scheduled to launch. What is the effect on the client?
A) The user-defined scan will be paused in order to launch the administrator-defined scan.
B) The administrator-defined scan will launch after the user-defined scan completes.
C) The user-defined scan will be canceled in order to launch the administrator-defined scan.
D) The administrator-defined scan will be skipped and the user-defined scan will continue.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which feature reduces the impact of Auto-Protect on a virtual client guest operating system?
A) Network Shared Insight Cache
B) Virtual Image Exception
C) Scan Randomization
D) Virtual Shared Insight Cache
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is a characteristic of a Symantec Endpoint Protection (SEP) domain?
A) Each domain has its own management server and database.
B) Every administrator from one domain can view data in other domains.
C) Data for each domain is stored in its own separate SEP database.
D) Domains share the same management server and database.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Where in the Symantec Endpoint Protection (SEP) management console will a SEP administrator find the option to allow all users to enable and disable the client firewall?
A) Client User Interface Control Settings
B) Overview in Firewall Policy
C) Settings in Intrusion Prevention Policy
D) System Lockdown in Group Policy
F) None of the above
Correct Answer

verified
Correct Answer
verified
Showing 101 - 120 of 165
Related Exams